Challenge #15 – tx.origin Misuse
Difficulty: High
#Security#AccessControl
This contract uses tx.origin for access control, which is insecure.
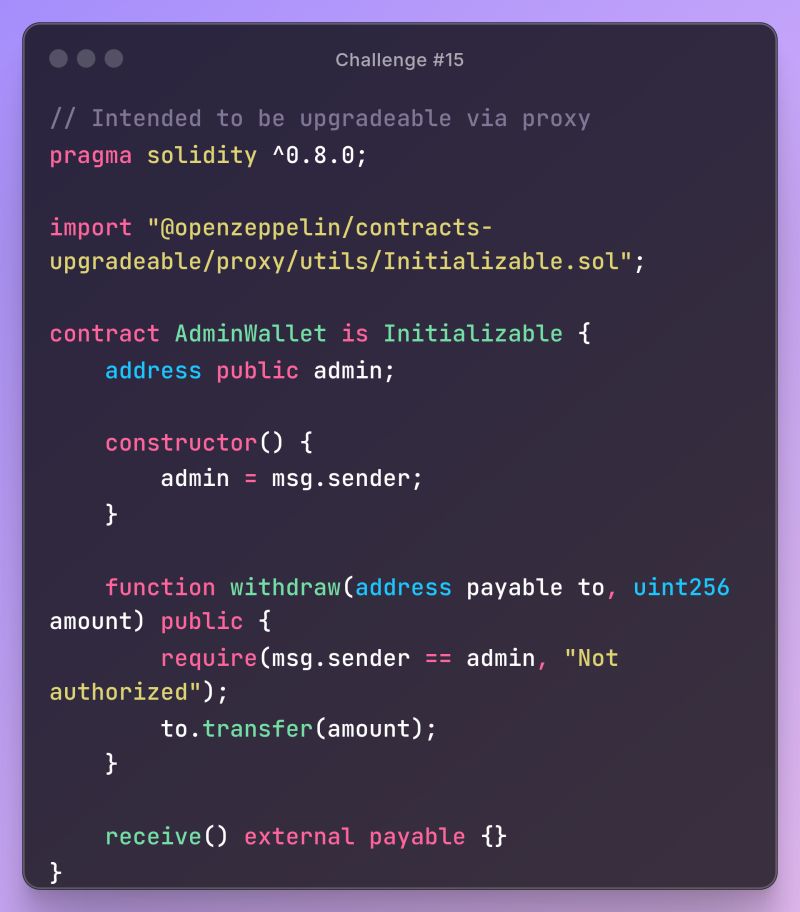
// Intended to be upgradeable via proxy pragma solidity ^0.8.0;
import "@openzeppelin/contracts- upgradeable/proxy/utils/Initializable.sol";
contract AdminWallet is Initializable {
address public admin;
constructor() {
}
admin = msg.sender;
function withdraw (address payable to, uint256 amount) public {
require(msg.sender == admin, "Not
authorized");
to.transfer (amount);
}
}
receive() external payable {}
💡 Hint: tx.origin can be manipulated. Prefer msg.sender.