Challenge #14 – tx.origin Misuse
Difficulty: High
#Security#AccessControl
This contract uses tx.origin for access control, which is insecure.
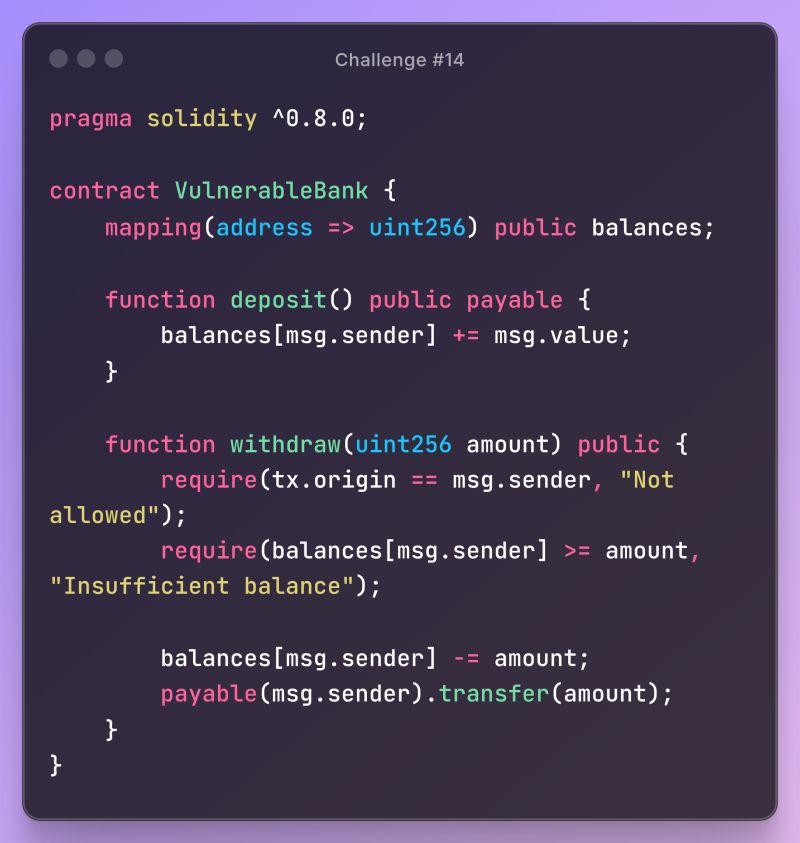
pragma solidity ^0.8.0;
contract VulnerableBank {
mapping (address => uint256) public balances;
function deposit() public payable {
balances [msg.sender] += msg.value;
}
function withdraw(uint256 amount) public {
require(tx.origin
allowed");
msg.sender, "Not
require(balances [msg.sender] >= amount,
"Insufficient balance");
balances [msg.sender] -= amount; payable(msg.sender).transfer (amount);
}
}
💡 Hint: tx.origin can be manipulated. Prefer msg.sender.